
Kaspersky, the multinational cybersecurity and anti-virus provider, made a startling revelation on May 10th. According to their report, a victim of a crypto hack had unwittingly purchased a counterfeit Trezor Model T from a “trusted seller through a popular classifieds website.” The researchers at Kaspersky were able to extract the custom firmware that the hackers had installed on the device. This revealed that the private key was already known to the hackers before the victim had even purchased the machine.
Cybersecurity Firm Kaspersky Investigates Phony Trezor Hardware Wallet
It seems crypto enthusiasts need to be extra cautious about counterfeit Trezor hardware wallets circulating in the market, designed with the malicious intent of pilfering cryptocurrency holdings. This unsettling revelation underscores the imperative for heightened prudence and attentiveness when acquiring hardware devices related to digital currencies.
Kaspersky, the Russia-based cybersecurity firm, exposed this disconcerting development on May 10, 2023, subsequent to an examination of a forged Trezor Model T that had successfully stolen a victim’s virtual funds. The unsuspecting victim acquired the counterfeit Trezor from a “reliable vendor on a well-known online marketplace.”
Furthermore, the device’s packaging was meticulously sealed and utilized Trezor’s tamper-resistant holographic labels typically affixed to their products. “At first cursory glance, the wallet we examined appeared to be exactly the same as a genuine one, and showed no signs of tampering,” stated the researchers at Kaspersky. Yet, on a fateful occasion, “a large sum of money was transferred to someone else” a few weeks after the victim loaded the wallet with their cryptocurrency assets.
In an intriguing twist, Kaspersky also revealed that the fraudulent hardware wallet executed unauthorized transactions without even being connected to a computer. “When handling the wallet, nothing felt suspicious either: all the functions worked as they should, and the user interface was no different from the original one. However, mindful of the theft that had occurred via it, we delved deeper,” explained Kaspersky.
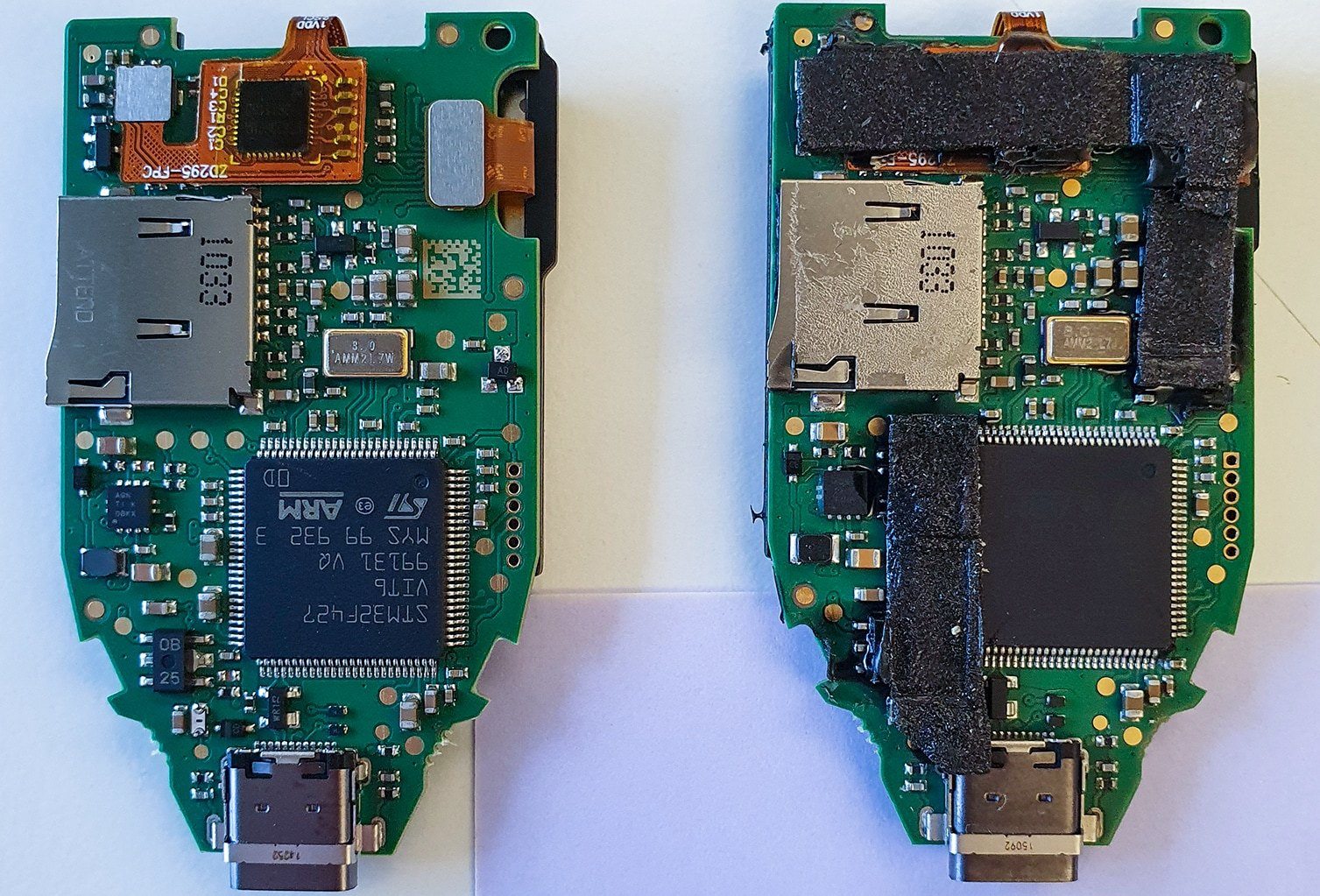
A notable cause for concern arose when the counterfeit Trezor was found to possess bootloader version 2.0.4., a bootloader release that was deliberately omitted due to previous instances involving counterfeit devices. Gaining access to the internal components proved challenging due to copious amounts of adhesive and tape, a stark departure from Trezor’s meticulous ultrasonic bonding technique.
Moreover, distinct traces of soldering were evident, alongside the presence of an “entirely different microcontroller.” Kaspersky unveiled that their experts successfully extracted the counterfeit wallet’s firmware and, through painstaking code reconstruction, made a startling revelation: “attackers indeed knew the private key in advance.” Armed with this information, the attackers could commandeer the funds through an alternate wallet employing the same private key, thereby pilfering the valuable assets.
“The fake crypto wallet would operate as normal, but the attackers had full control over it from the very beginning,” Kaspersky detailed. “According to the transaction history, they were in no hurry, waiting a whole month after the wallet was credited for the first time before they grabbed the money. The owner had no protection whatsoever: the game was lost from the very moment the money first arrived in the Trojan wallet.”
The recent revelation serves as a stark reminder that individuals invested in cryptocurrencies must exercise heightened vigilance to safeguard their valuable digital assets. Over the years, attackers have honed their techniques for pilfering crypto holdings, presenting an ever-present threat.
While hardware wallets have long been regarded as a trusted solution, users must now grapple with the risks entangled within the intricate web of supply chains and so-called reputable vendors. Kaspersky’s groundbreaking discovery underscores the pressing need for individuals to exercise utmost diligence when entrusting significant sums of funds to a hardware device.
What steps do you think crypto enthusiasts should take to protect their digital assets from the growing threat of counterfeit hardware wallets? Share your insights and strategies in the comments section below.
Image Credits: Shutterstock, Pixabay, Wiki Commons, Kaspersky
Disclaimer: This article is for informational purposes only. It is not a direct offer or solicitation of an offer to buy or sell, or a recommendation or endorsement of any products, services, or companies. Bitcoin.com does not provide investment, tax, legal, or accounting advice. Neither the company nor the author is responsible, directly or indirectly, for any damage or loss caused or alleged to be caused by or in connection with the use of or reliance on any content, goods or services mentioned in this article.







